Wireshark From Scratch
- ca-member
- May 21, 2023
- 3 min read

What is Wireshark?
It is one of the most famous necessary tools for network engineers. It supports Windows and macOS, and basically captures installed packets on the PC to make it visible easily.
It is often being used when network investigation in troubleshooting, etc.
Download and Install
In the official site (https://www.wireshark.org/), download the supported OS file.

When it finishes downloading, open the execution file, click “Next” by following the installer.
(↑ you can leave the default settings)
Once installation is done, open Wireshark, and it’s completed if you see the screen below.

Double click on the network adapter that looks like a wave and take a look at the capture of the main connected interface.
How to look up Windows capture data
As soon as you choose an interface, it shows captured inbound/outbound packets. (I hide IP and other sensitive information.)

It makes no sense.
To try it out, let’s ping to our website (beyondjapan.com) from the command prompt.
> ping beyondjapan.comType “icmp” in the search bar on the top and then press enter.

It sorts only the results of ping and can check ICMP packets to our website.
Right click on the bottom of strings > choose “expansion everything”, you can check the details of the packets.

The orange part: Source/destination address, router model and MAC address, etc.
The green part: IP versions (In this example, v4 and header length)
The pink part: Flags, TTL and protocols
The red part: ICMP types and checksums
This time it’s ICMP that there’s not much information, but as long as the packet is not encrypted, you can see the payload and other detailed data.
This is another example
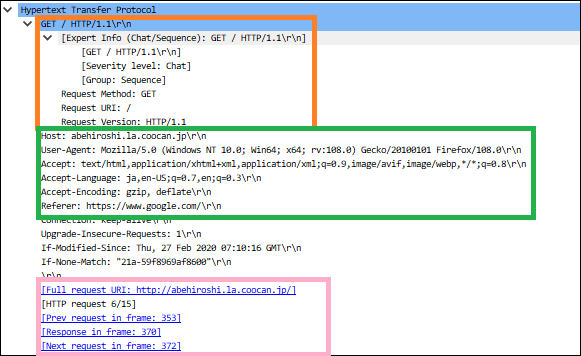
The orange part: Request method and PHP version
The green part: Host information, browser’s user agent information, language, referer, etc.
The pink part: Access URL and frame numbers associated with the accesses
What you need to be careful of is the information entered in a form.
When you send a password when it is not being encrypted, someone else can see the password strings from packet capture.
(This is why you shouldn’t use public Wi-Fi)
About filters
Wireshark descriptions are used for the search.
In this article, I introduce a notation that is often used. Since it can be written in a variety of ways, including regular expressions, it may also be useful for troubleshooting when interacting with the API.
・Filter by IP address
ip.addr == xx.xx.xx.xx
!(ip.addr==xx.xx.xx.xx) #exclude specific IP addressFor the experiment, search the result of the ping sent to “1.1.1.1”.

You can check the interactions of ping request → reply.
・Filter by the port numbers
tcp.port == xx
udp.port == xx
tcp.port == xx || udp.port == xx #multiple look up with or
!(tcp.port == xx) #exclude specific port
!(tcp.port==xx) && ip.addr==xx.xx.xx.xx #and termCheck TCP/443 communications as a test.

If you check IP, you can check data when you use Google search.
If you look at the description and flags part of the “Info” section, you can see the TCP handshake exchange (ACK, FIN, etc.).
Linux machine’s packet capture
If you have a PC with Wireshark installed, you can view the packet capture files obtained on your Linux machine.
This time, I’m going to use tcpdump.
(You need to install tcpdump using yum or apt)
In this article, I used Ubuntu to create an arbitrary file and output data. Write the data to a file named “test.pcap”(pcap is an extension of the packet capture file).
Check and specify the name of the interface which is an interface that communicates via the route from a local or intranet network towards An interface that communicates via the route from a local by using ifconfig.
> tcpdump -i ens33 -w test.pcapThe capture continues until you cancel, so you need to generate the communication you wish to check while it is being captured (browser access, etc.)
End the tcpdump and move the output file to a Windows/macOS machine.
Open the extracted pcap file with Wireshark to make captured data visible.

Now the packet of Xmas scan is visualized.
Wireshark's strength is that anyone can easily capture the flow of packets as long as you know how to read them.
In addition to the PC you are using, you can also capture all packets flowing in the local network through a switch and create a mirror port, so this software is popular at work.
It is also useful for studying TCP/IP, so please install it.
This blog post is translated from a blog post written by Kawa Ken on our Japanese website Beyond Co..




Comments